Azure AD as Client Provider in MuleSOFt
Dynamic client registration to configure Azure Active Directory (Azure AD) client management with Anypoint Platform. Using Azure AD as a client provider enables you to authenticate and authorize API consumers with your existing configurations. Azure AD configuration in Anypoint Platform also provides a stateless microservice to convert OAuth 2.0 client application registration requests to requests supported by Azure AD. Lets see how we add Azure AD as client provider in Mulesoft.

To show how we can configure this in Anypoint platform, please follow below steps
Login to Azure portal and click on Active directory
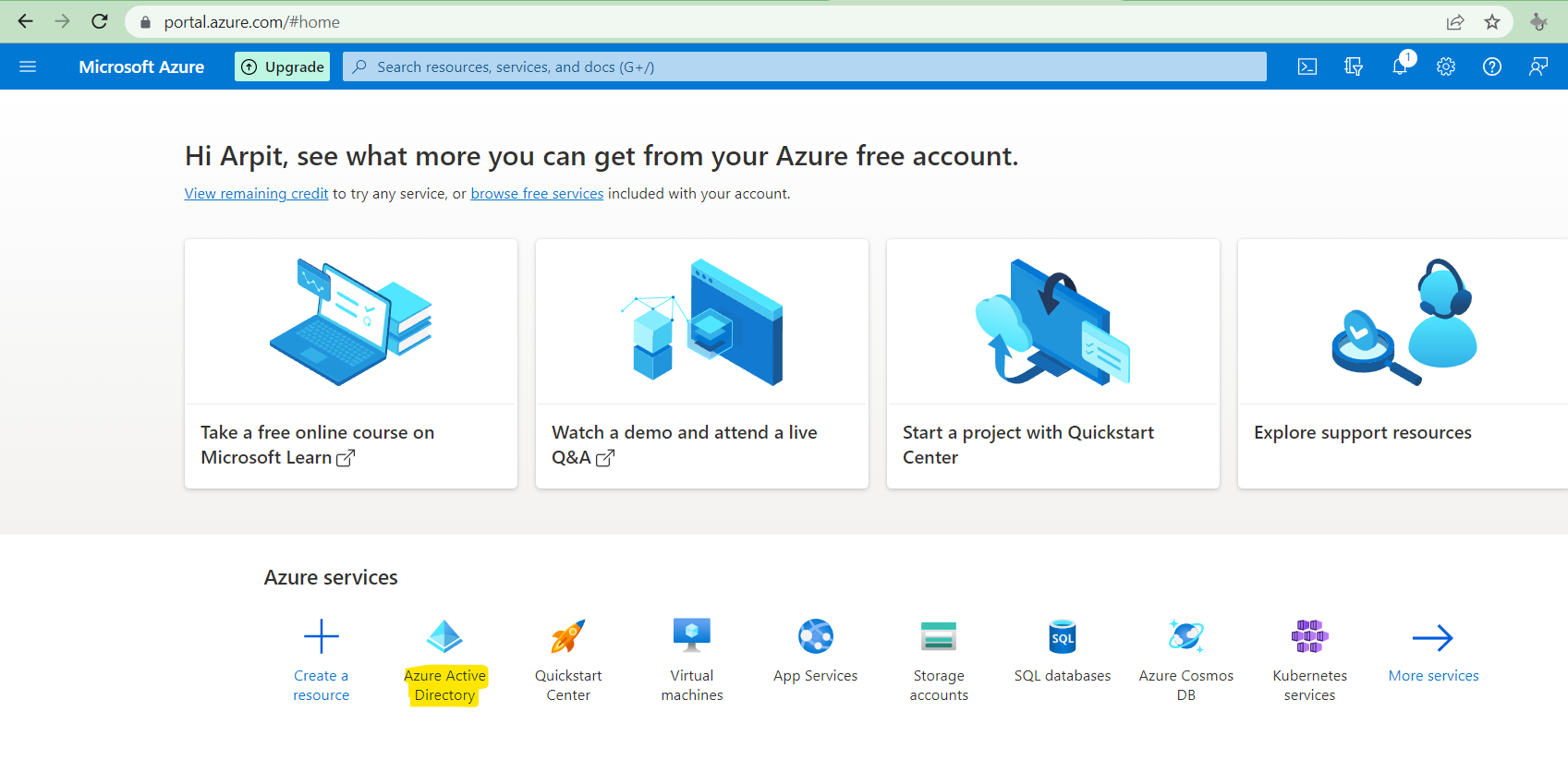
Click on App registration
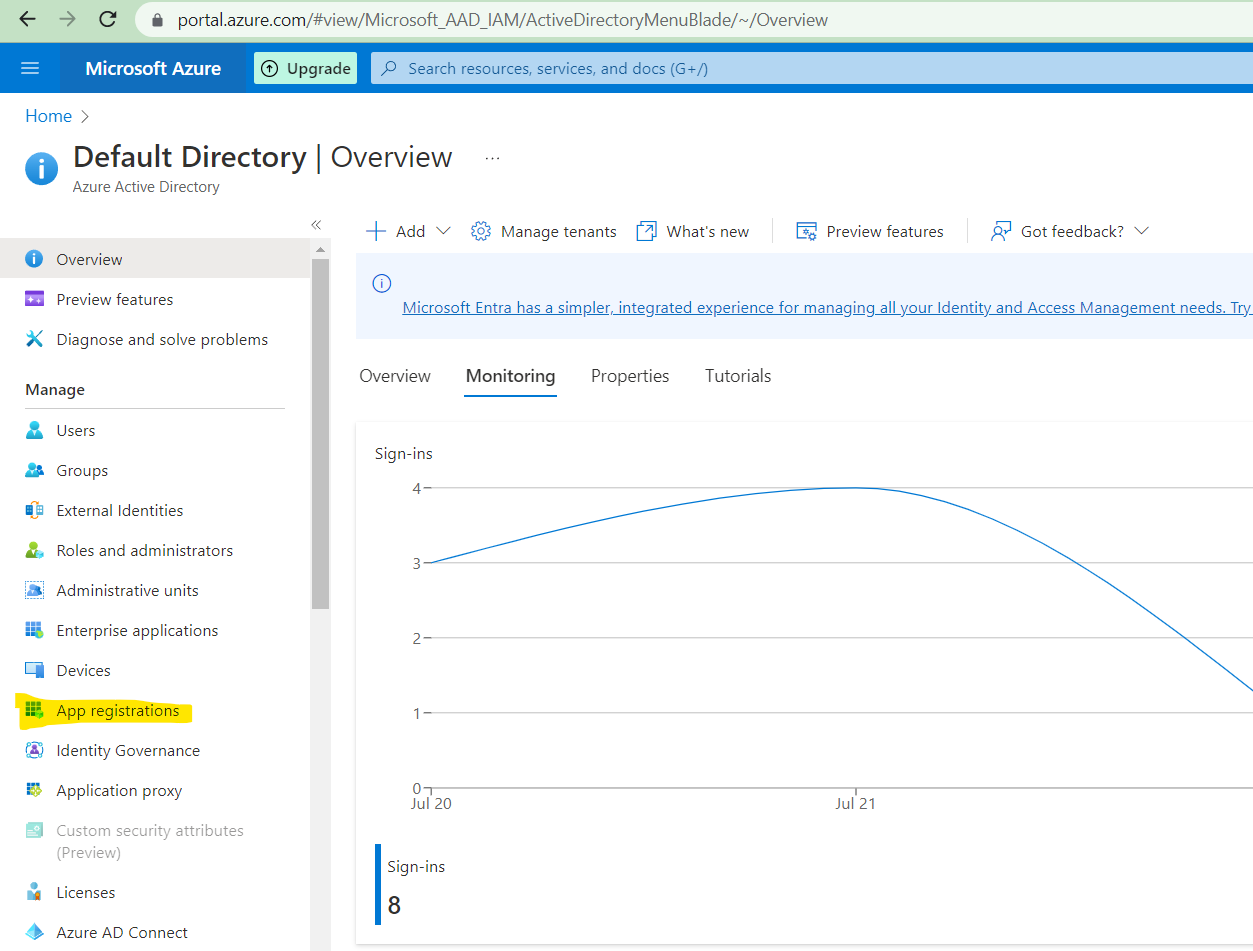
Click on new registration
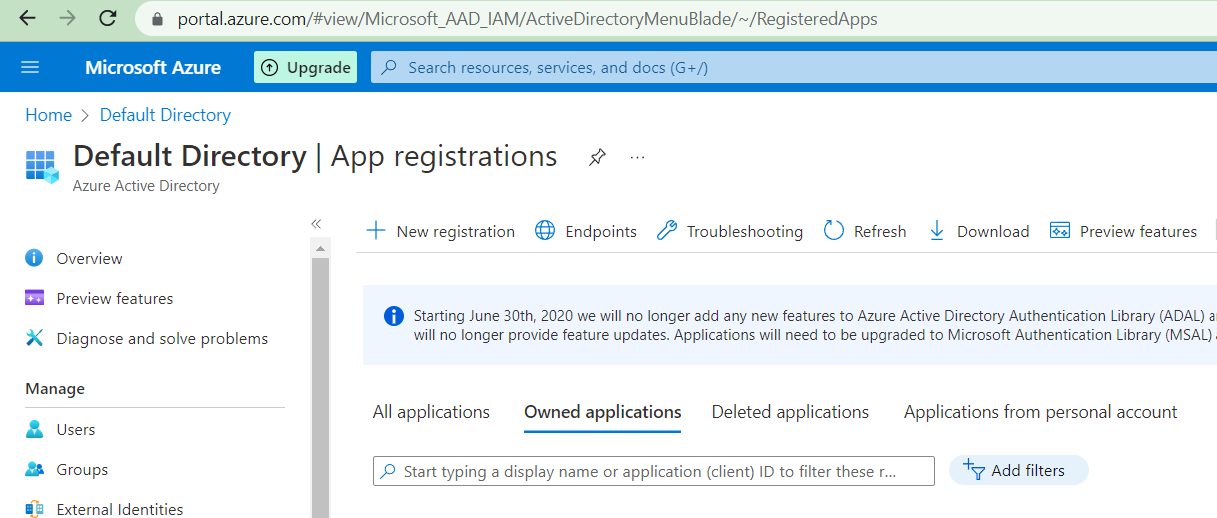
Add the details and click register
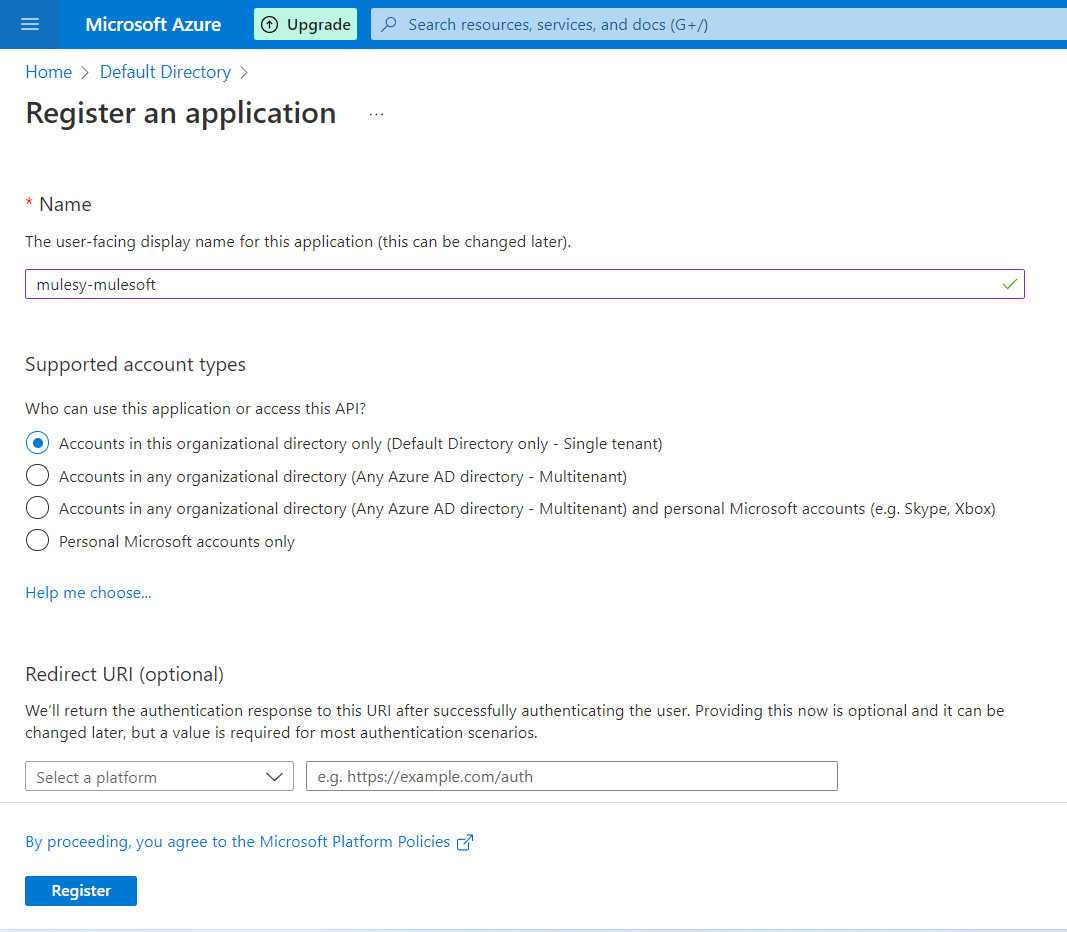
Copy client id and tenant id
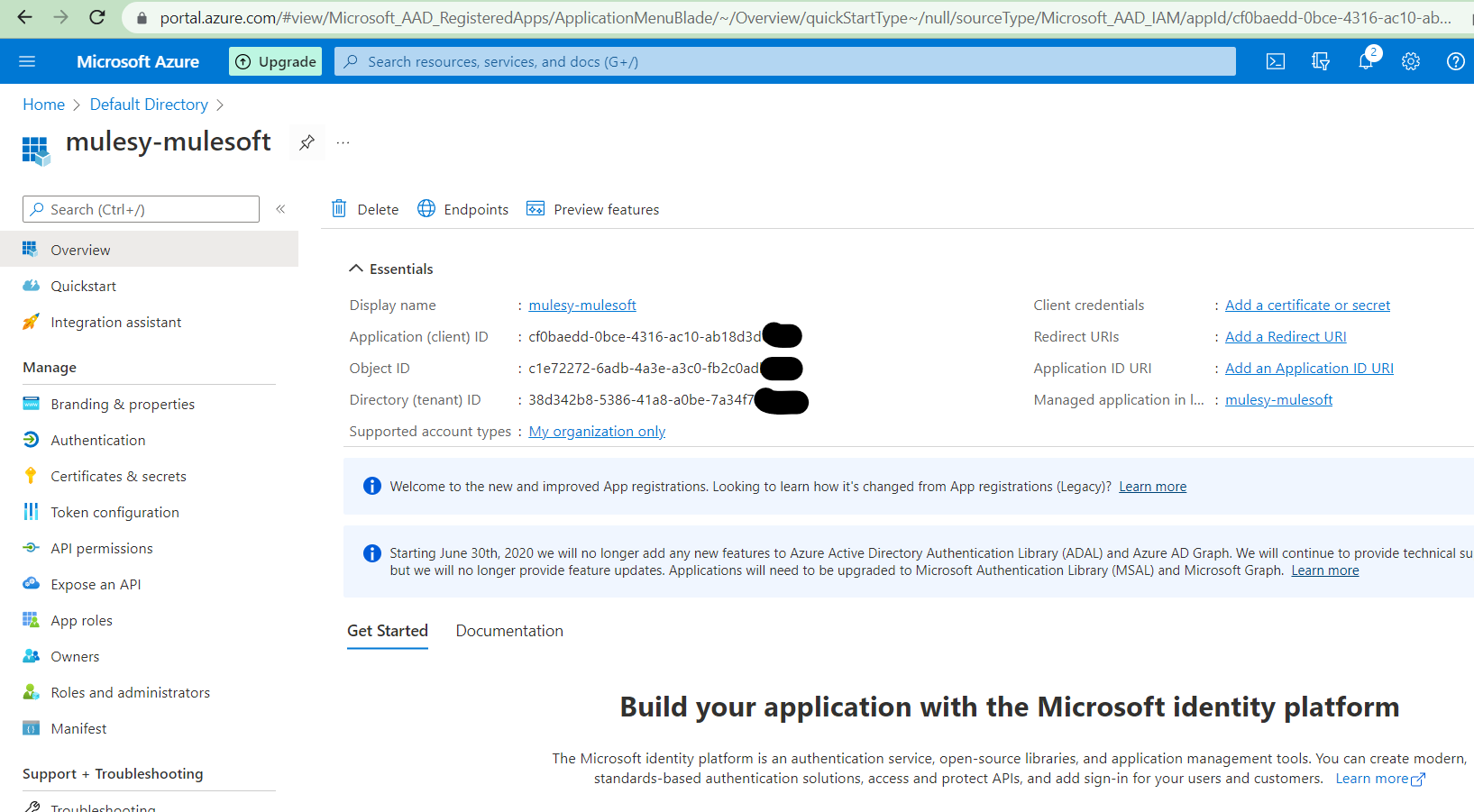
Click on endpoints and copy WS-Federation sign-on endpoint this will act as issuer id in client management configuration
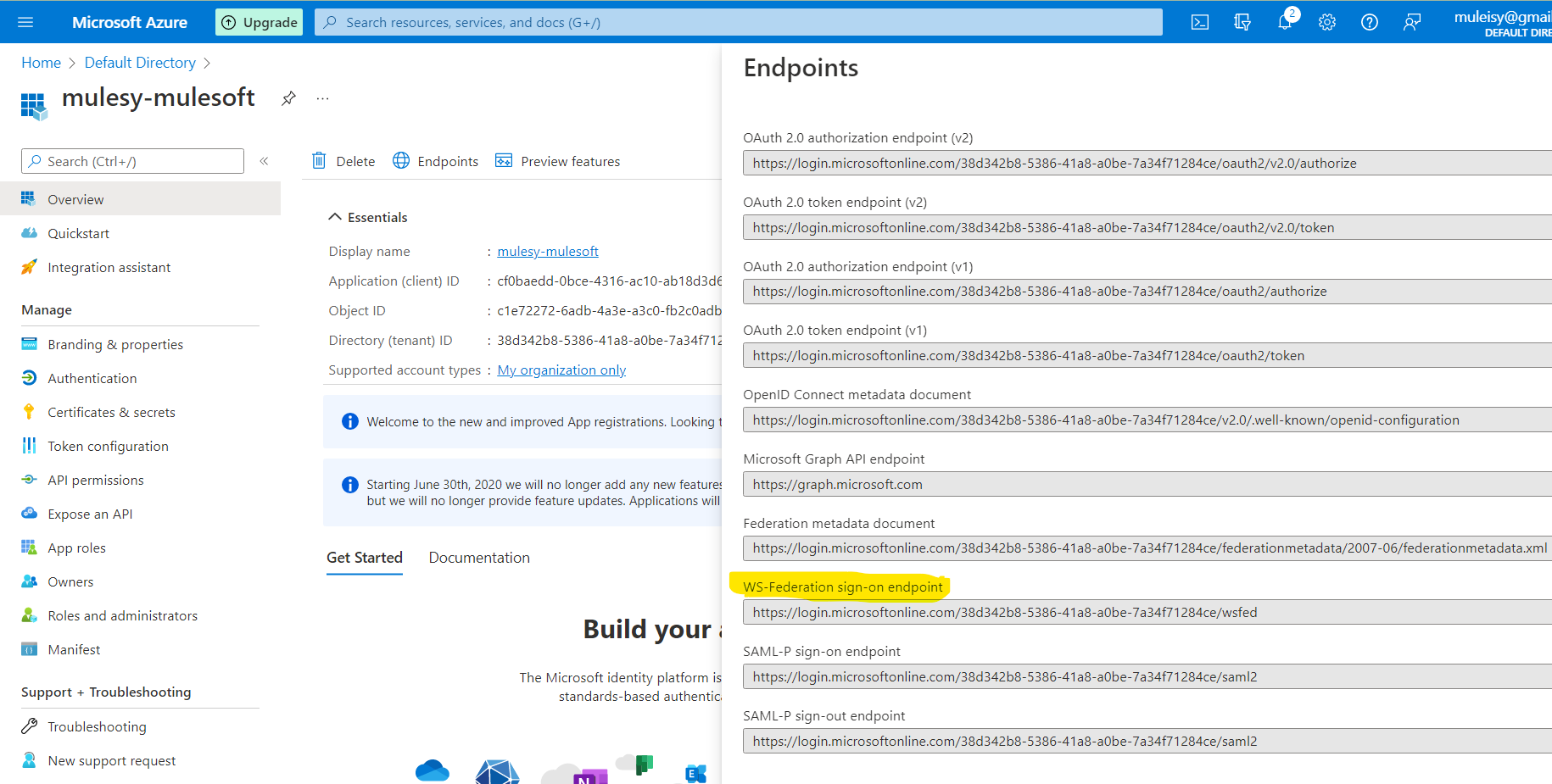
Click on certificate and secrets -> new client secret
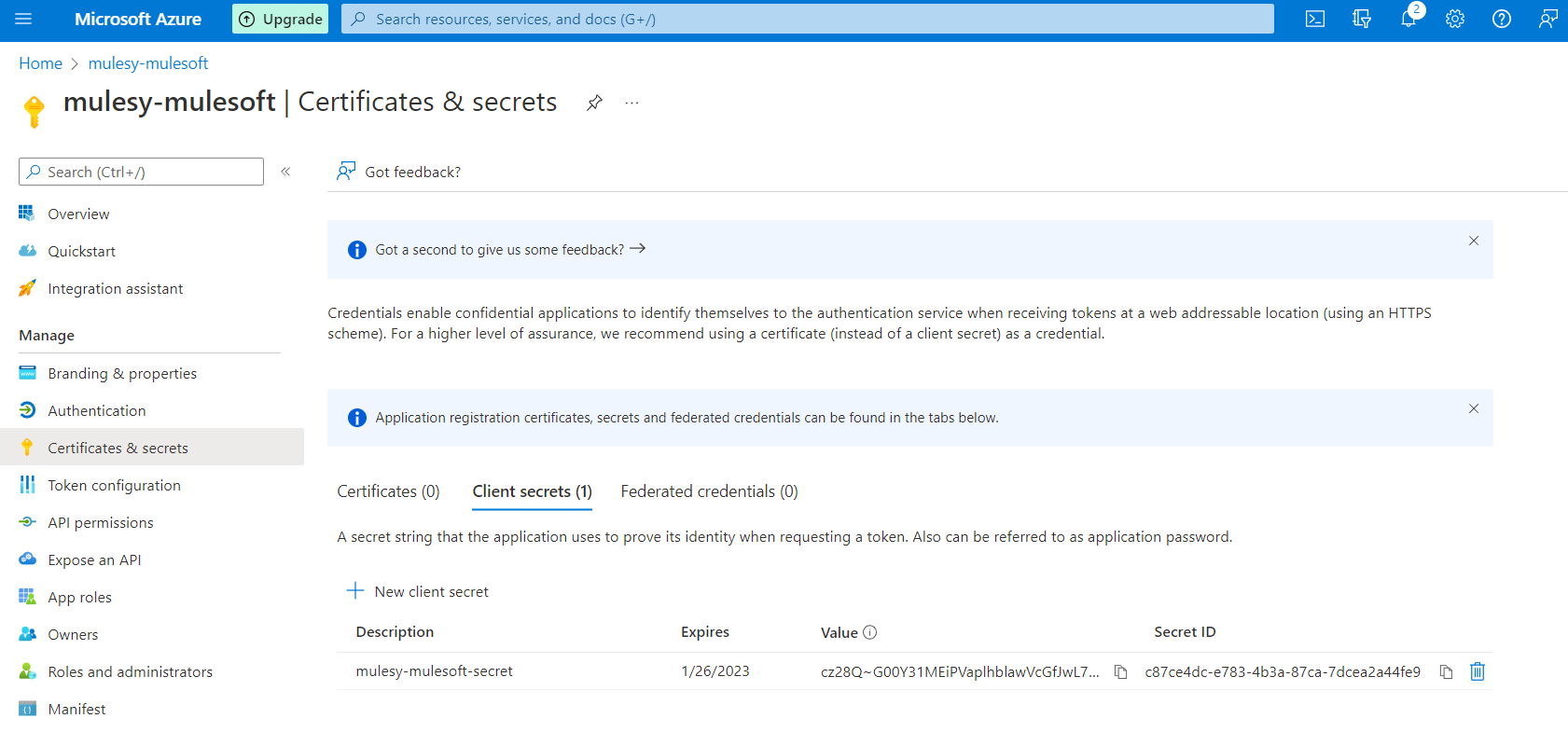
Copy the secret value (value will be shown only once so copy and save it to secure location)
Now click on API permission and click add permission
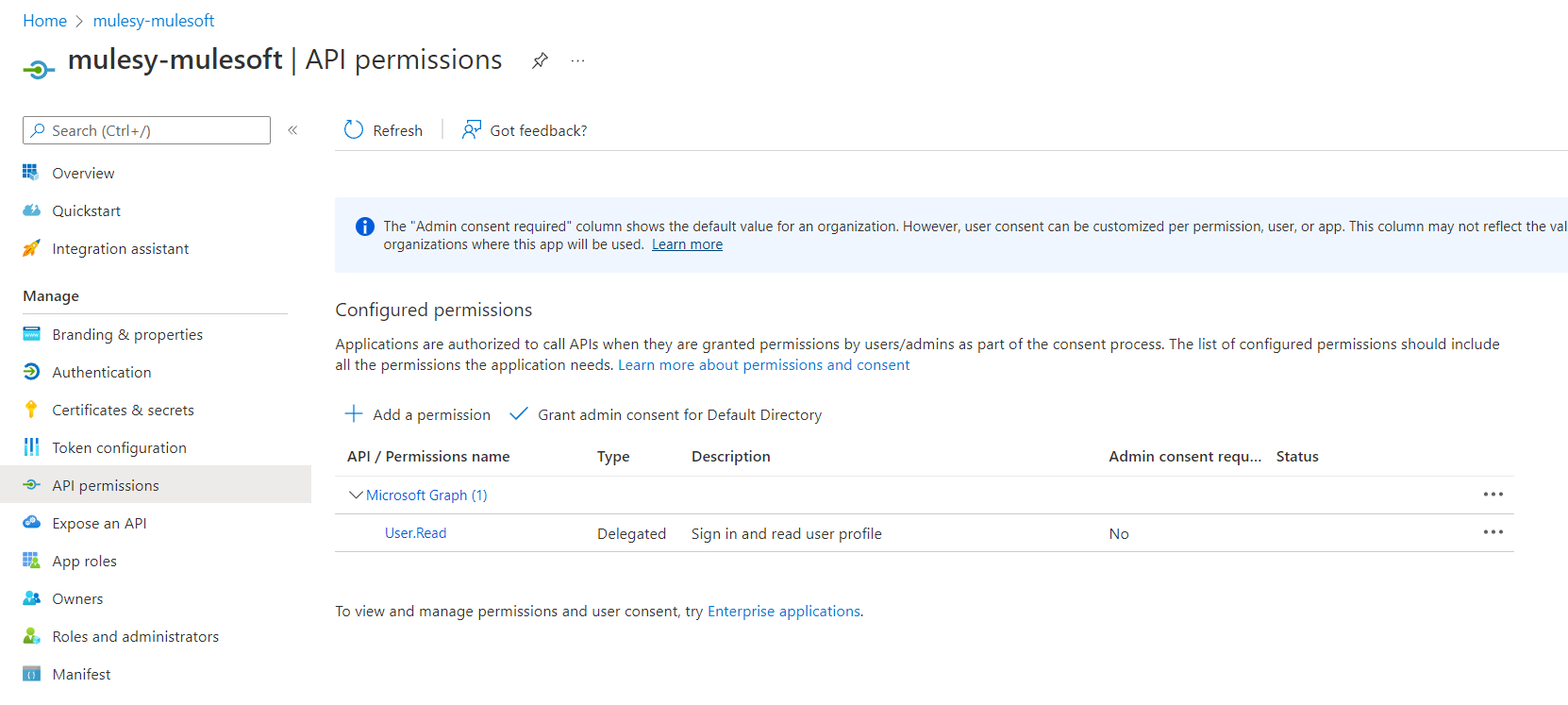
Add all the permission shown as below
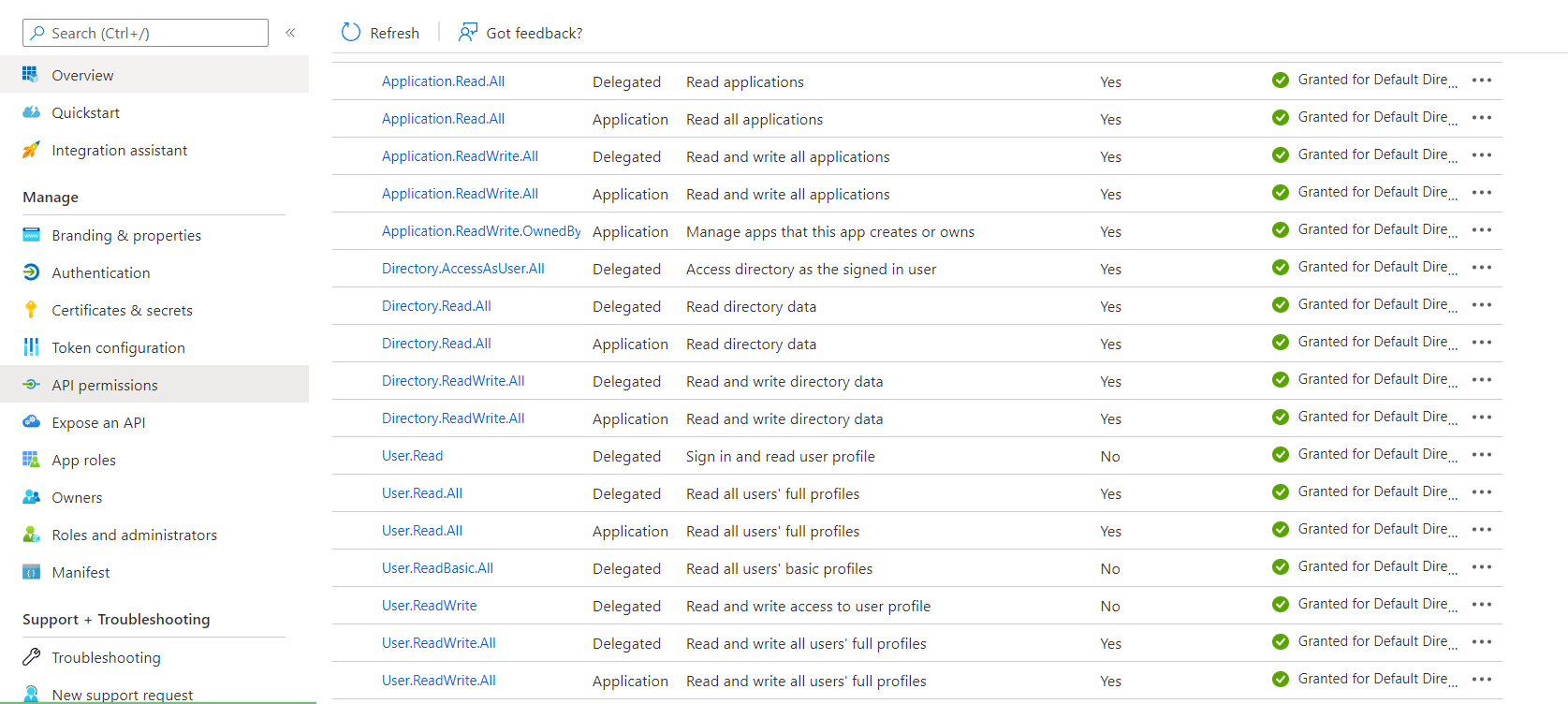
Once added click on grant admin access for default directory
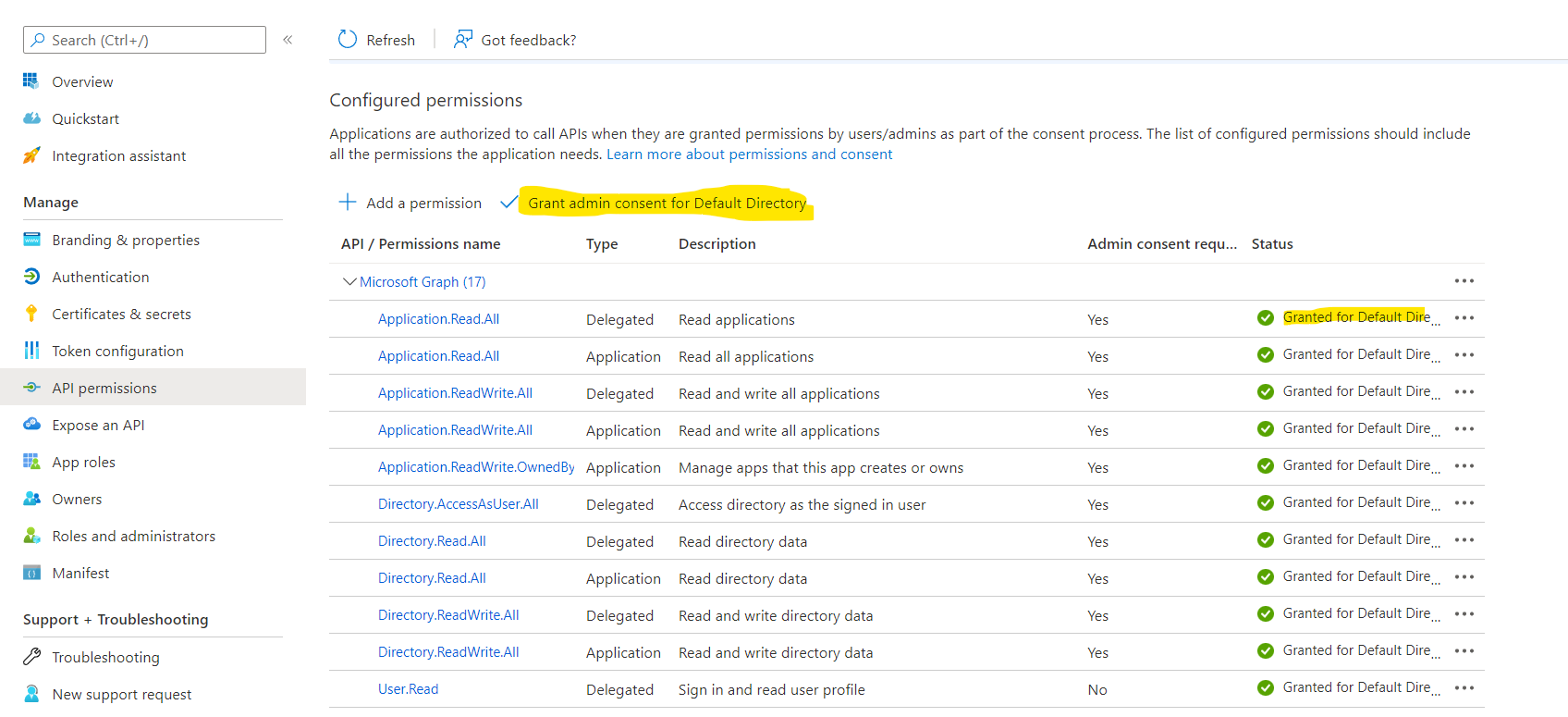
With this we are now done with the azure configuration and can now do the required configuration on Anypoint platform
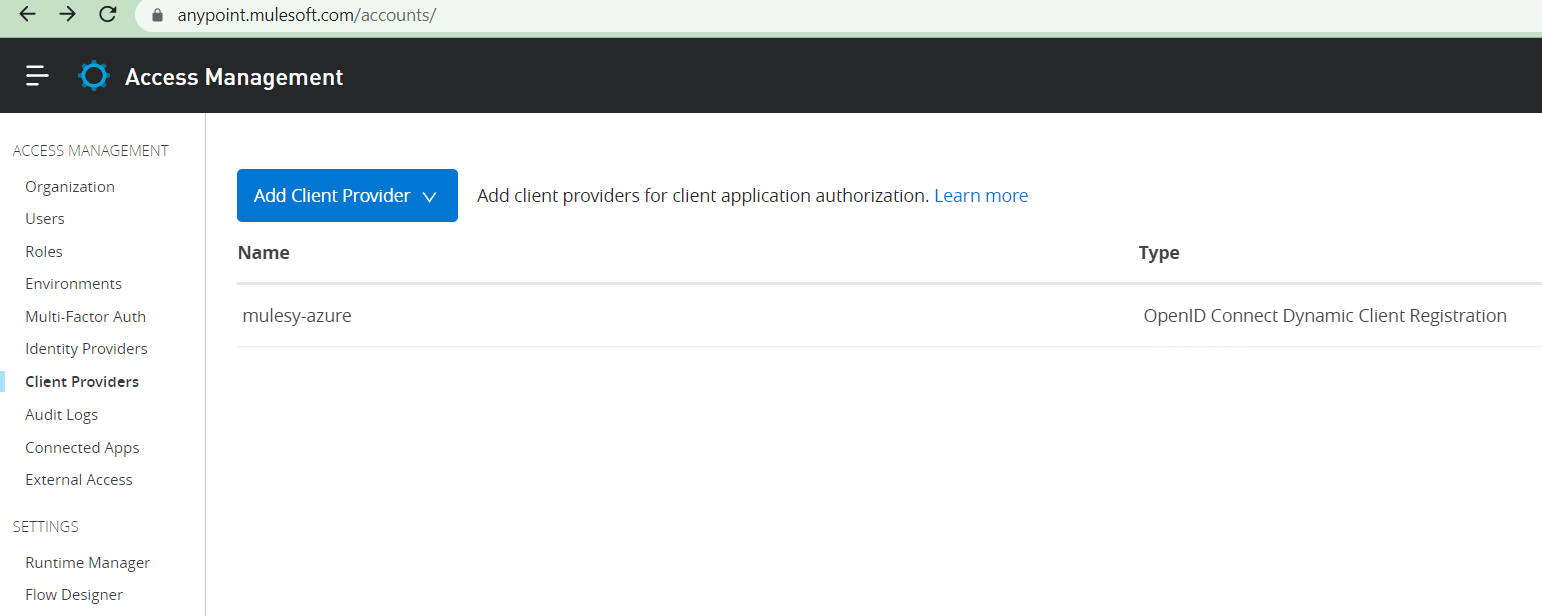
Click Access Management -> Client Providers -> Add Client Provider -> OpenID Connect DCR for Azure
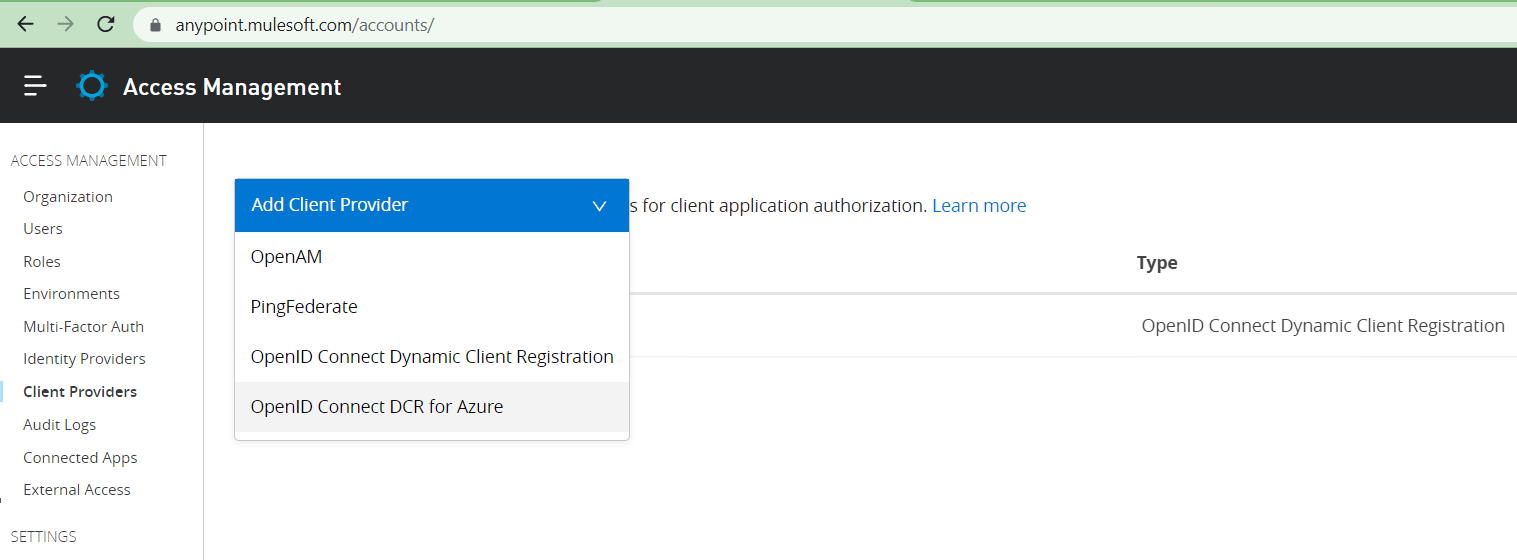
Add the details
Issuer – WS-Federation sign-on endpoint
Tenant Id, Client Id and Client Secret from the Azure portal
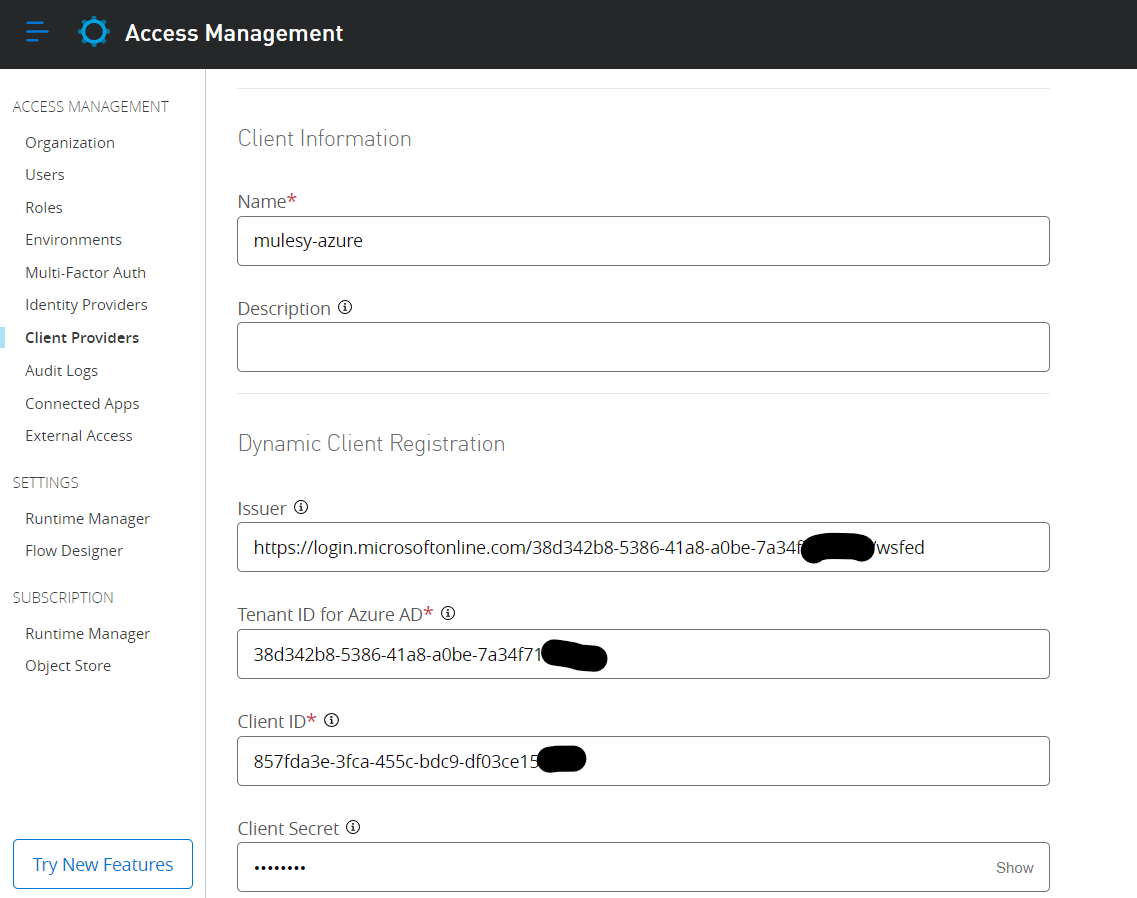
Click on Create or Save

This will create the configuration
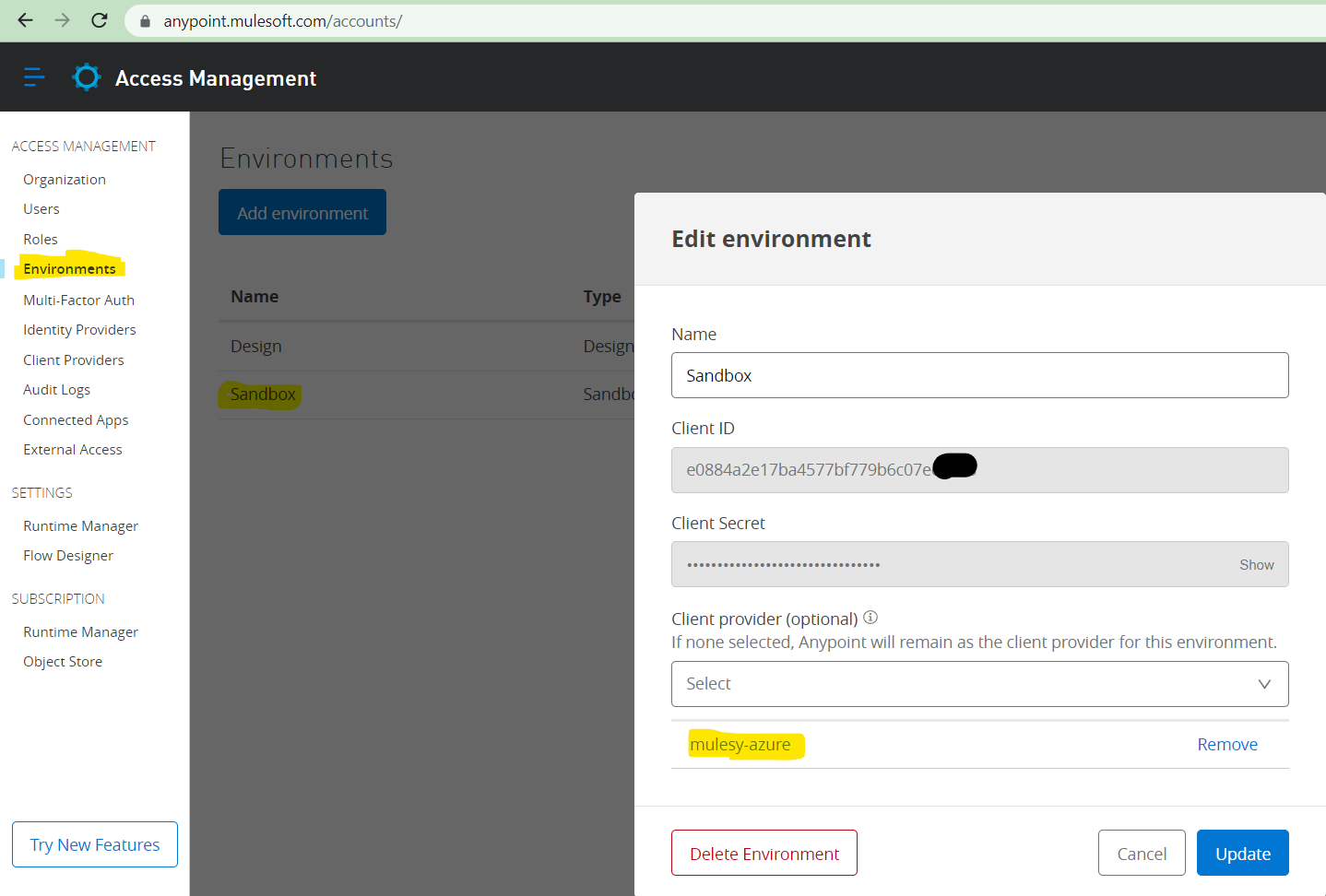
Click on the Environment and select the environment where we want to add it as client management and click on update
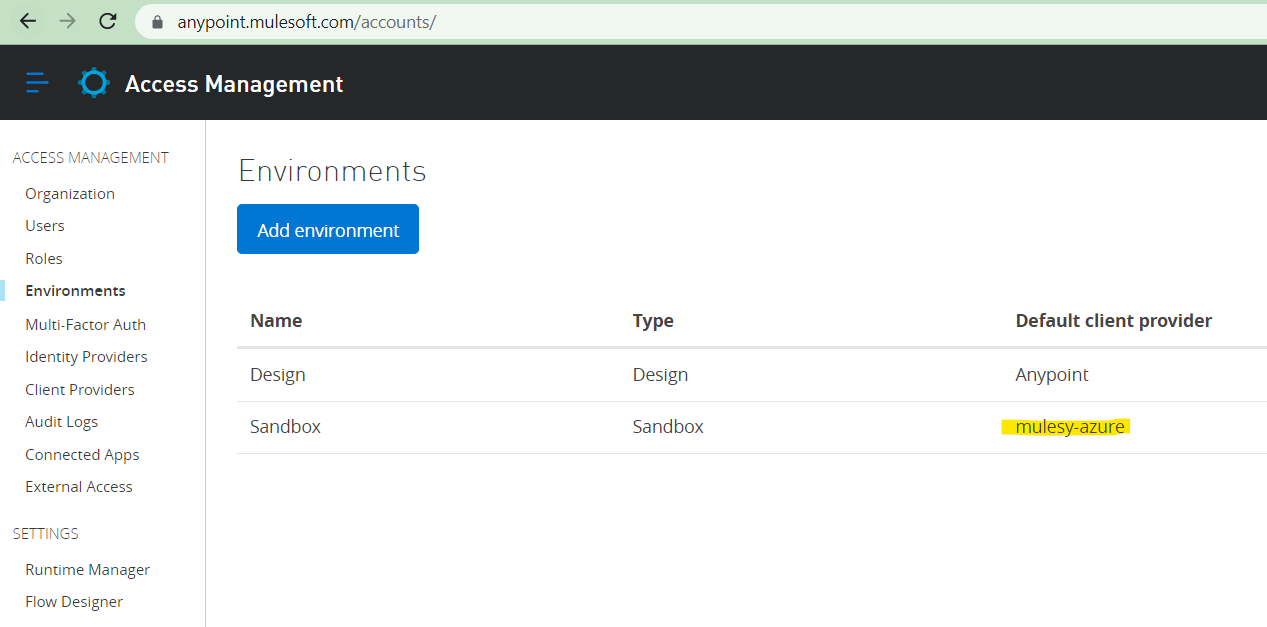
Environment configuration is updated now
Now we have add the OAuth policy to our api in Anypoint Manager
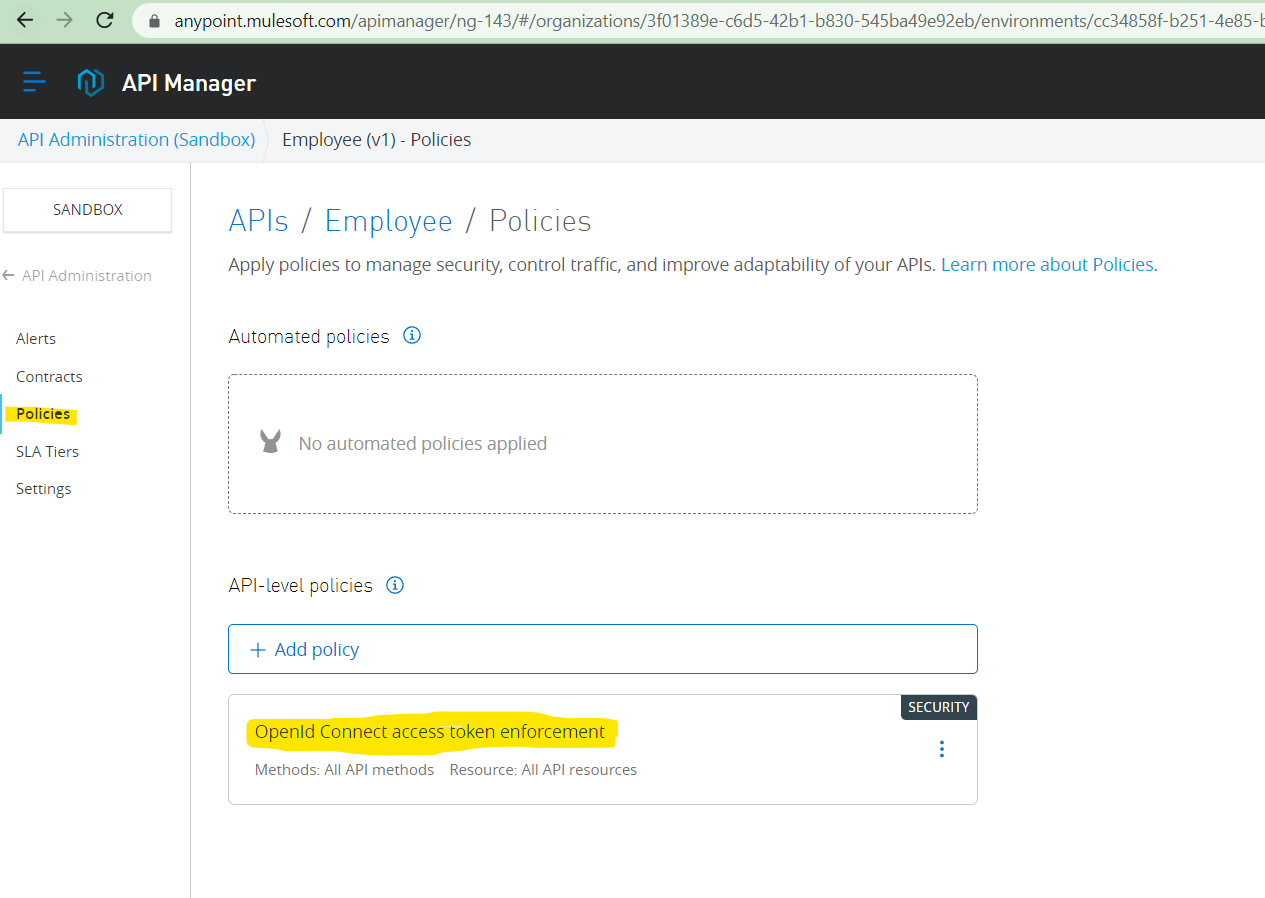
How to connect API manager with runtime application – please see how we can connect the mulesoft application to API Manager
Now we will create the client app to call the employee API
Go to Exchange and select the relevant API and click on Request Access
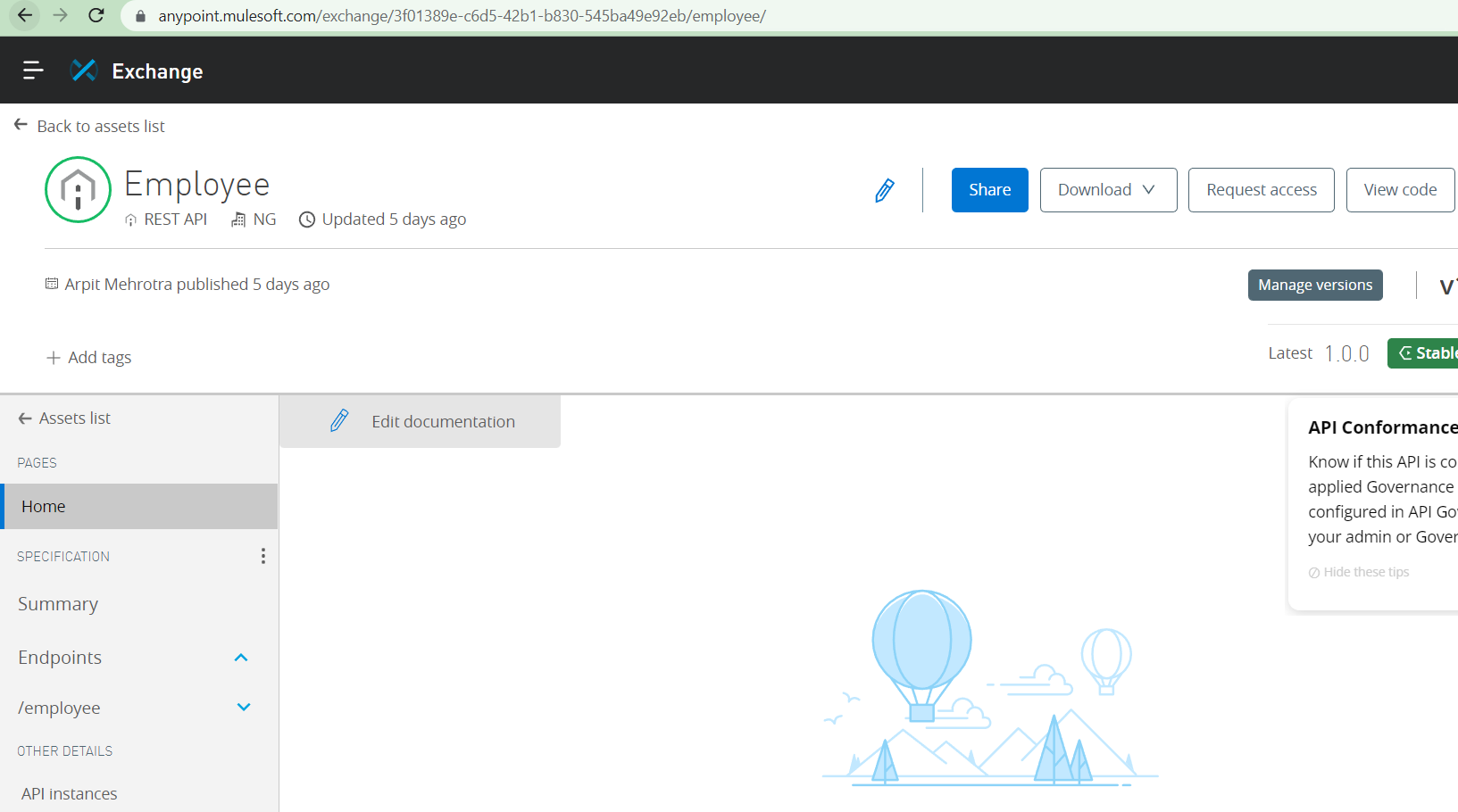
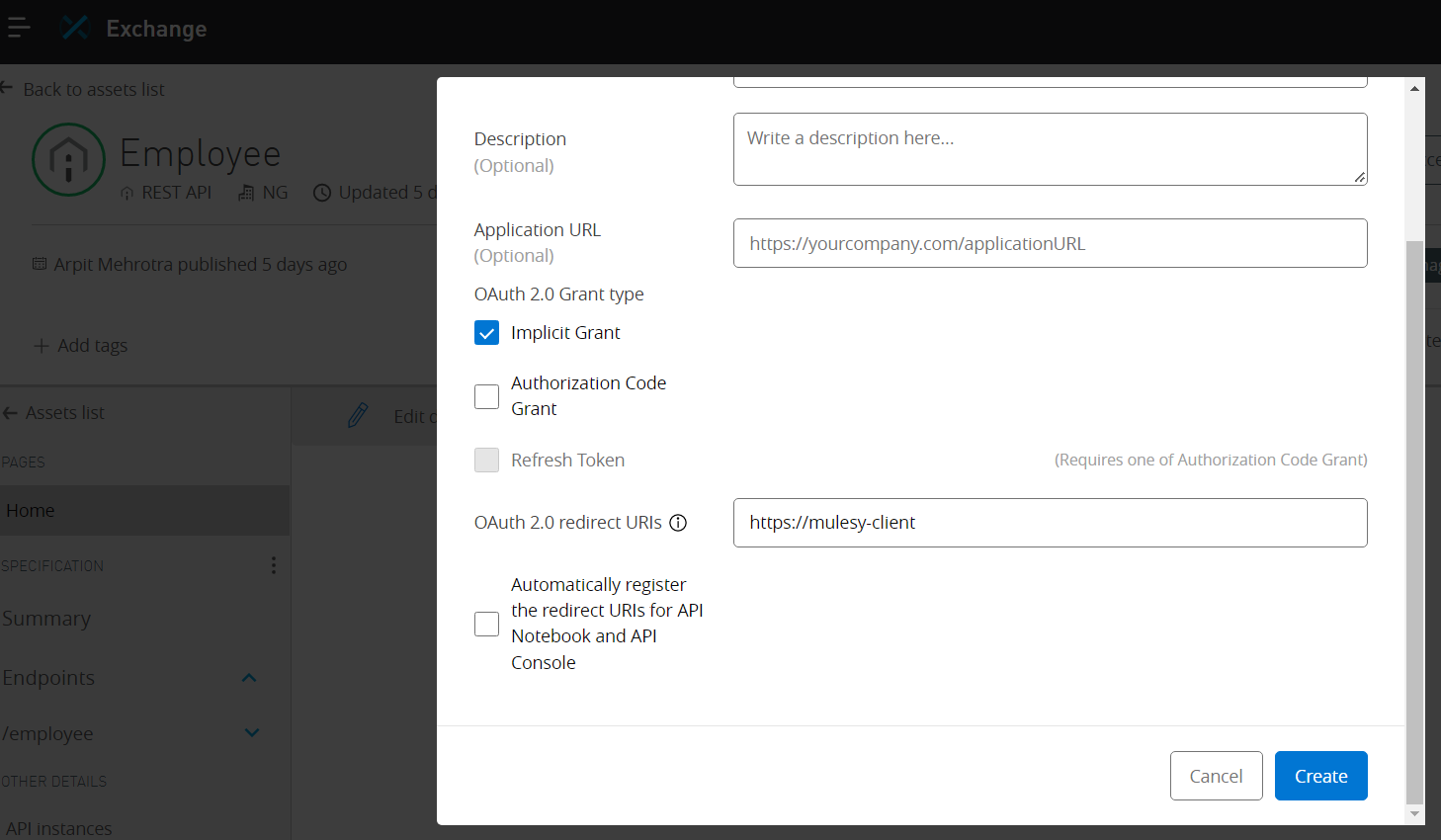
Select create new application
Add the details
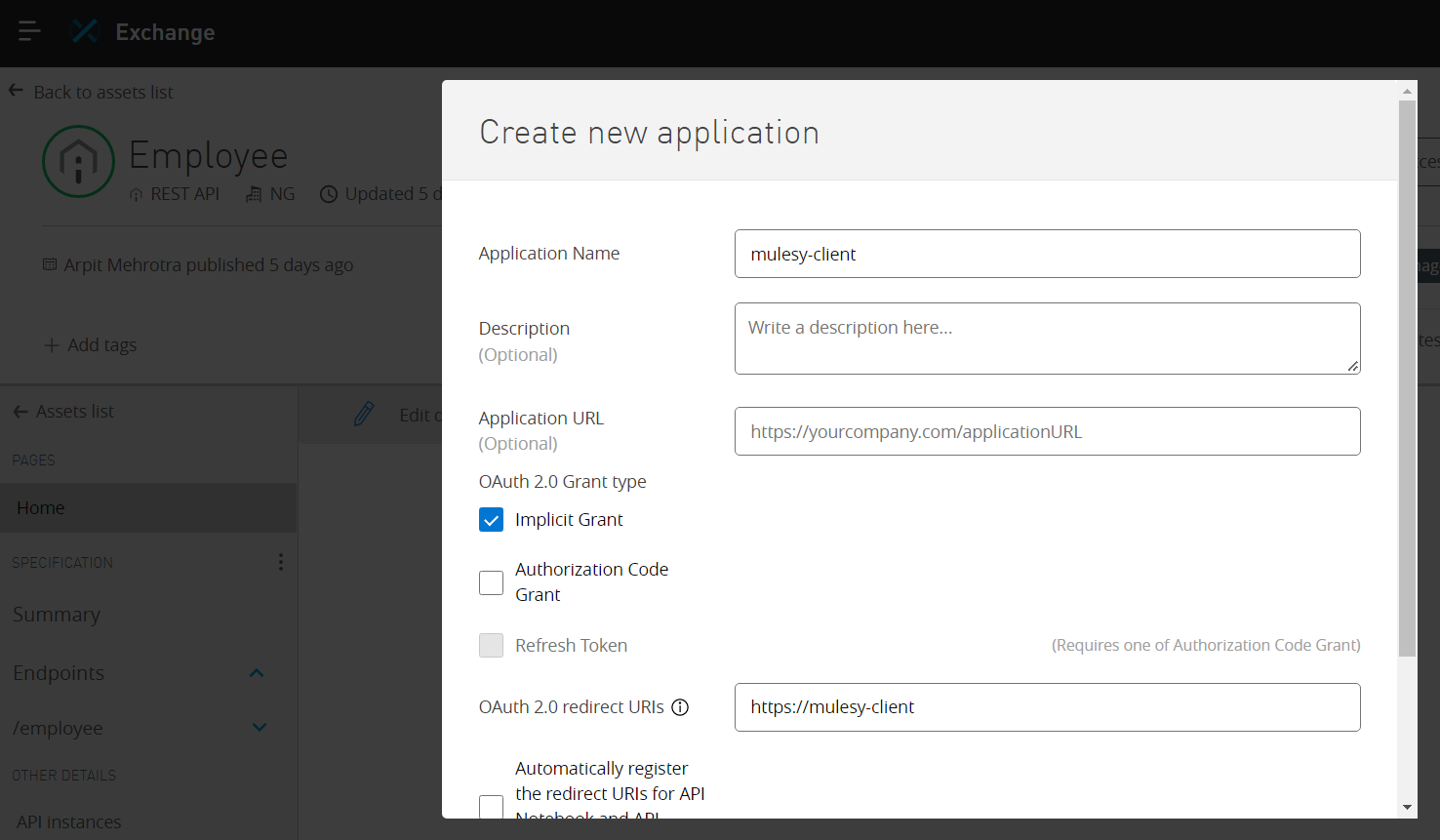
And click on create
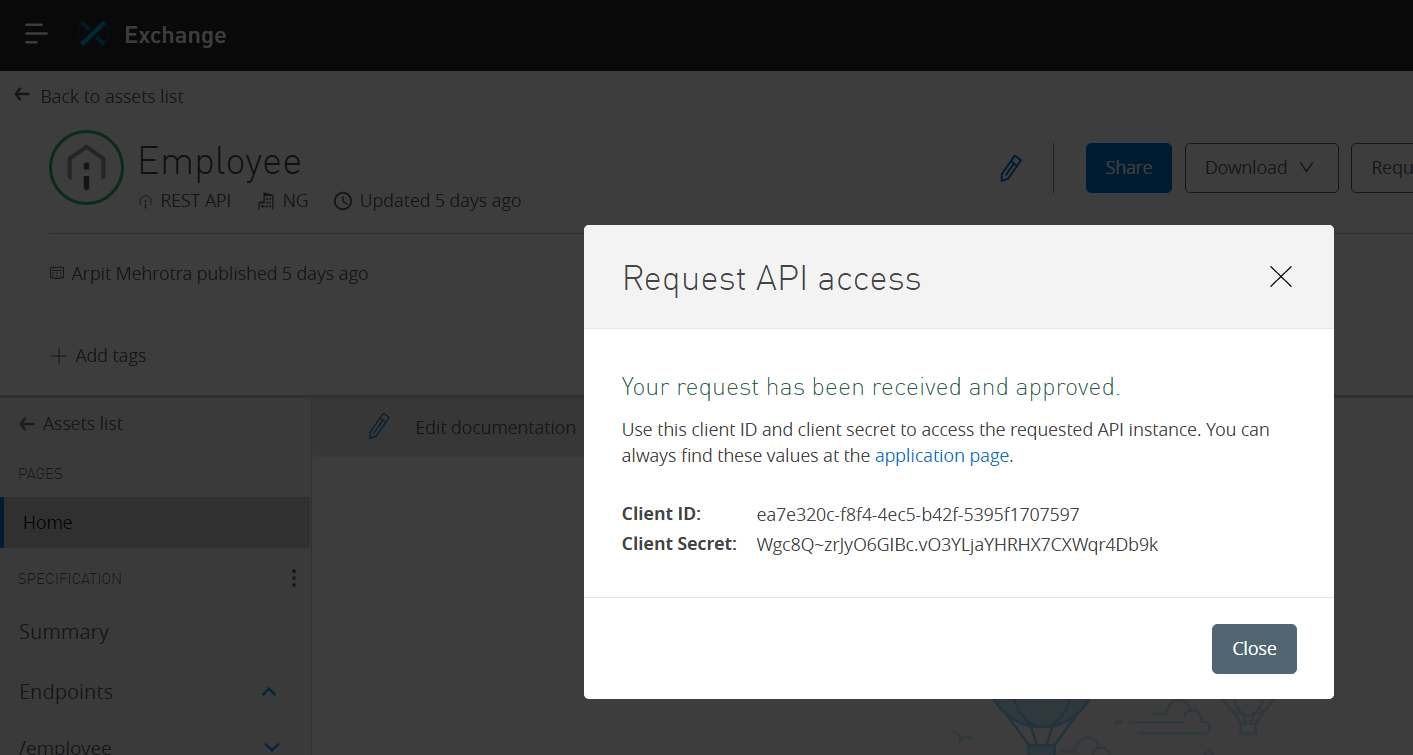
Click on Request Access

It will show the Client ID and Secret
Sometime it might give HTTP 500 error so just retry
Same Client app will be created at the Azure side as well
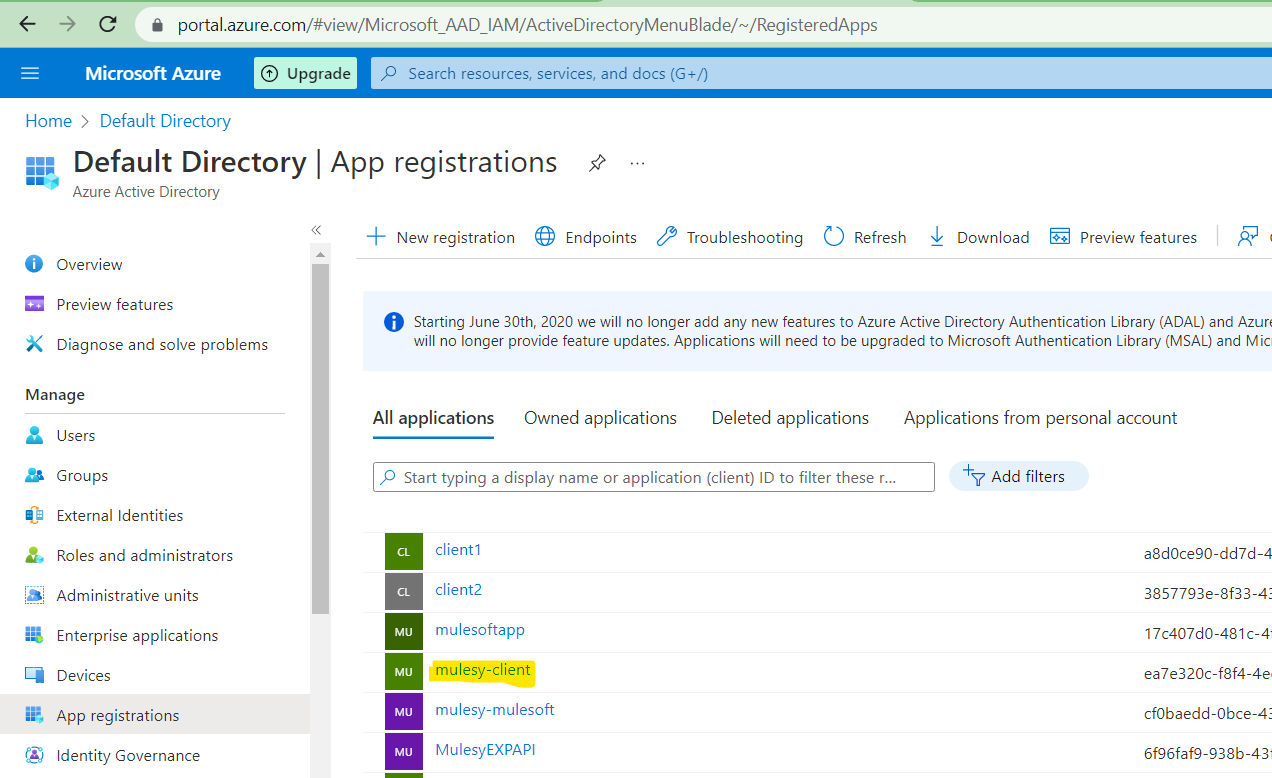
This show the client app is now dynamically created on Azure side
Now if we call the employee API from postman we can see the error “Access token was not provided”
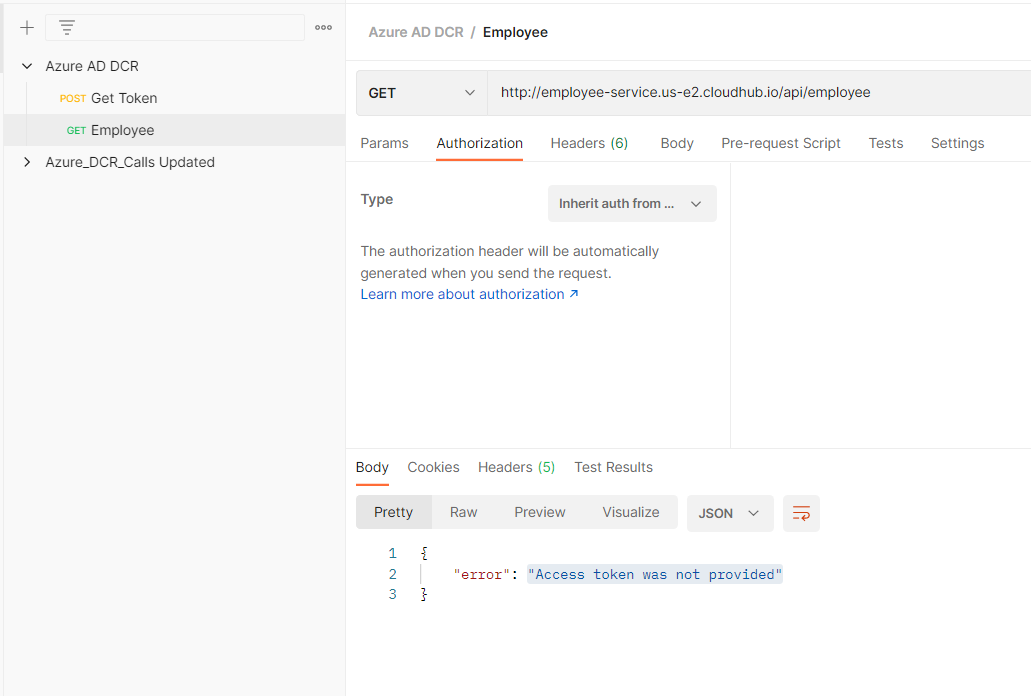
Now we will call the Azure AD to get the token
To make a call we have to use below details
- authorize url: https://login.microsoftonline.com/{tenantId}/oauth2/v2.0/authorize
- token url: https://login.microsoftonline.com/{tenantId}/oauth2/v2.0/token
- client id: {your client id}
- client secret: {your client secret}
- scope: https://graph.microsoft.com/.default
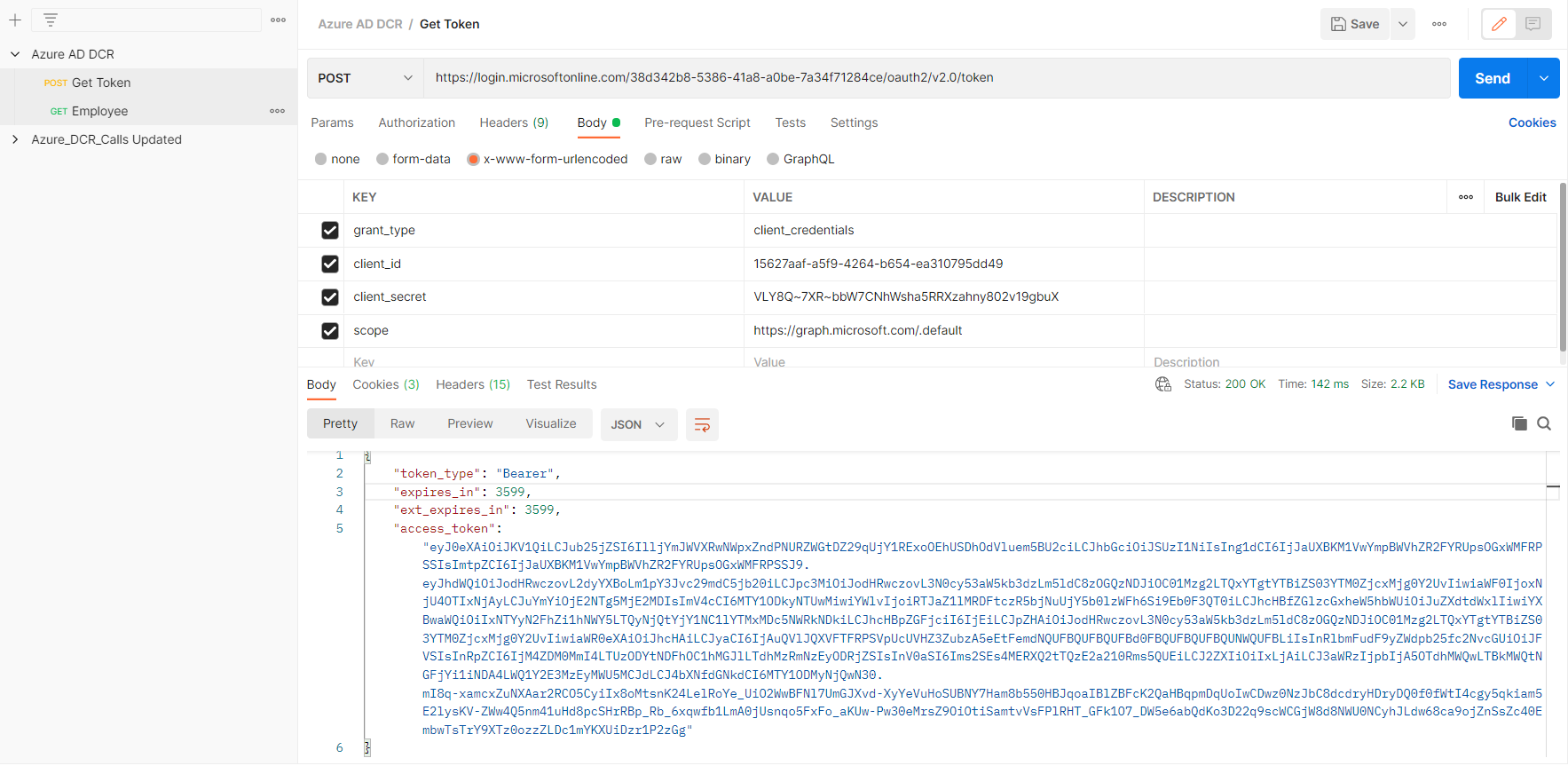
Will use the token and call the actual employee api
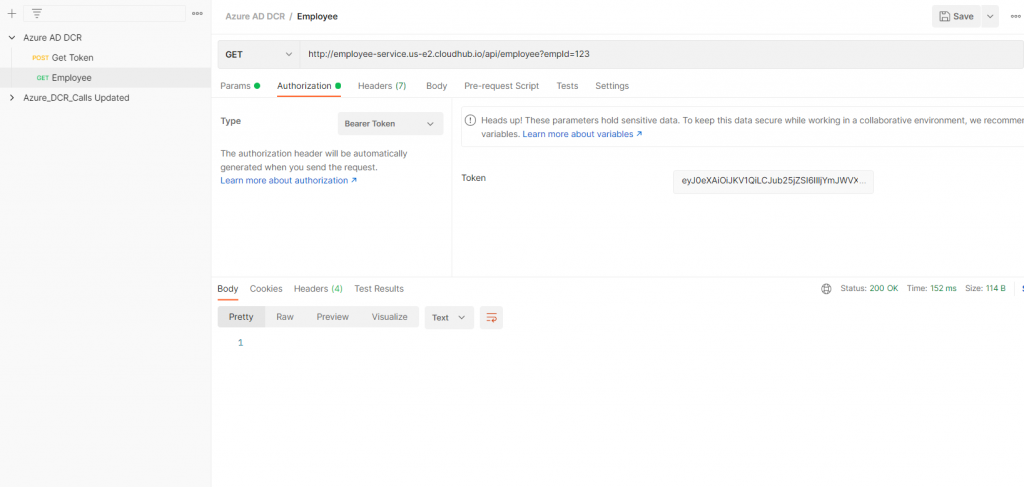
So we can see the clients app are dynamically managed on Azure side.
Sample POSTMAN collection – Azure AD DCR.postman_collection
Nice, Very informatic and useful one!
Where do I find the Employee API mention in this exercise?
I’m unable to validate a scope using this configuration with the OpenID Connect DCR for Azure client provider configuration using the OpenId Connect access token enforcement policy. Is there a solution?
I am unable to find “OpenId connect access token enforcement” policy in API manager, could you please help me how can we git it installed in API manager?
It’s only visible once you configure the client identity in Anypoint platform.
Hello, I have one question concerning the token request call:
To make a call we have to use below details
authorize url: https://login.microsoftonline.com/{tenantId}/oauth2/v2.0/authorizetoken url: https://login.microsoftonline.com/{tenantId}/oauth2/v2.0/tokenclient id: {your client id}client secret: {your client secret}scope: https://graph.microsoft.com/.default
Where and how do you use the authorize url?
How to setup the oauth token expiry time?
Default is “expires_in”: 3599